Hackers Know Your Password: Don’t Stay Vulnerable

The leakage of the Largest Credential Database
Scandals associated with the theft of passwords and personal data happen regularly - only in the past couple of years the passwords of popular mail services were leaked to the open network, and even the services for storing passwords were hacked.
1.4 Billion passwords were found in a single database - how can you be sure that yours is not there? In this article you will find out what kind of threats your password is open to, and how to protect your personal data with the correct credentials.
All passwords are presented in text form, and the most terrible fact is that most of them are passed as acceptable. Almost all users, interviewed by researchers, confirmed that the passwords were valid.
Researchers compared the data from the leak to other known bases
It was discovered that, although most of the credentials were already known, 14% of the login/password pairs had never been found before.
This new database adds 385 million new accounting pairs, 318 million unique users and 147 million passwords.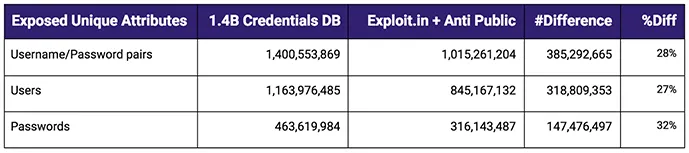
Since the data is organised in alphabetical order, the main problem is easily detected - the reuse of passwords: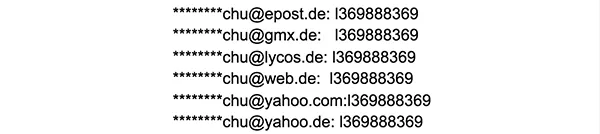
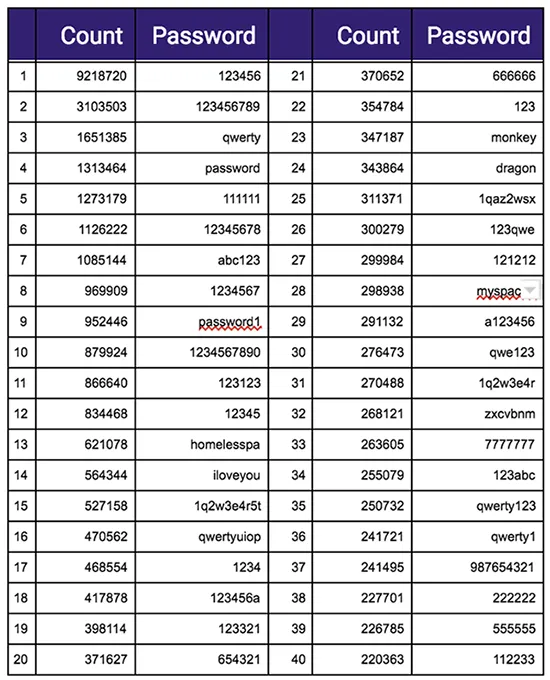
Here is the list of 40 most popular passwords:
How Do Hackers break passwords?
There are always at least two ways to crack the password:
- A trivial selection, which takes a huge amount of resources and time, but with the proper luck, will not take an hour.
- The most simple and effortless way is the "pet attack.” This is when people choose the name of their pets as a password, making it very easy for hackers.
Recommendations for passwords and their compilation

Actually, in order to complicate the process of hacking a password, a large number of recommendations applicable to its selection and compilation are singled out. We will try to give only some, the most important ones.
Fighting QWERTY
Lower your eyes to the keyboard and see how these keys are located. No doubt, you noticed that they are running in a row. So never do such nonsense. Do not allow more than two characters running consecutively in the password.
For example, passwords like
When choosing a password, try to avoid alternating characters (alphabetically or by keyboard layout), this can save you from hacking by selection.
Collisions - What Is It and How to Avoid It
When you come up with the key for encryption, try to avoid such nonsense as repetition of symbols. In itself, the word Collision is already a lousy password, in it we have two consecutive letters L . When encrypted, it will give a lot of duplicate characters. And the repetition of the same character in the password makes it much easier to select.
No matter how much you like it, try to avoid repeated symbols and use the same letters in your password.
Length vs. Efficiency

Some people believe that the names of Icelandic volcanoes are excellent passwords. And let's be honest, are you ready to memorize 15 characters of text, about which you can break a language? And often there are more than a lot of collisions and ordering of symbols in these names.
Compare on the above parameters 2 simple passwords (conditionally simple, of course):
- Faithful
- Yokalatarakoyl
Let's see what we have in both cases and what disadvantages there are:
- A small number of characters, one alphabet is used, no numbers. However, all the symbols are quite scattered in alphabetical order and layout. And in the password we have 6 effective symbols.
- A large number of characters, one alphabet, no numbers. However, in this password we have two letters "k", "y", "o" and "l". We have four letters "a" at once. Therefore, in fact, in this password there are 6 characters.
You do not need to be a wisecrack to figure out that these passwords are equally reliable, regardless of the number of characters that are used in the second. Therefore, we can safely say that the password is such a thing, where the quantity is very rarely intertwined with quality.
Using Numbers
But how to make the first password more effective? - Simple, but effective advice - to add the numbers.
- Adding to the word "Loyalty" something like "11111" or "666" is, of course, a solution, but generally ineffective. We add more symbols to remember, and we increase the efficiency only by one.
- It is best to follow the rules applicable to letters to pick up 3-4 figures. So, for example, the password "Loyalty1859" will contain 10 effective symbols.
- Each account requires its own password. Even if one of the passwords appears unreliable, hackers won’t get access to all your accounts at once.
More complicated and better-protected passwords are the combination of small and capital letters, numbers, special symbols, collected in non-predictable order.
The last, but not the least: do not keep your passwords auto-saved by the browser on your computer or smartphone - it’s the easiest way for hackers to reach them. If you have some points to be discussed - contact our London team or just come for a lovely chat with a cap of tea.





